About Zirgy
[+]

export@shzjsmart.cn

Address
3F, Building 1, 875 Qiuxing Road, Pudong New District, Shanghai
Library management system
Application background

The application of RFID in library magement

Construction target
| 1 | Search and locate: Achieve the rapid positioning of books in the library and quickly search for books. |
2 | Improve efficiency: The application of library management system will effectively eliminate the workload of the frontier personnel, increase working effeciency and increase the document management ability. |
||
| 3 | Smplify procedure of borrowing and returning: Realize an intelligent book borrowing and returning process, and improve the security of information storage, the reliability of information reading and writing, as well as the high speed and convenience of borrowing and returning books. |
4 | Book anti-theft: With the help of RFID technology, achieve the monitoring of the entry and exit of books, and achieve anti-theft alarm for abnormal departure from the library. |
||
| 5 | Improve service: Increase the level of satifaction of borrowers, and release library staff from the daily heavy and repetitive labor. |
6 | Sort and shelf: The portable RFID reader makes it easy to find the books that are not on the shelves or are misplaced, making the shelf-organizing work more accurate. |
Construction emphasis
The construction of this system will develop an excellent RFID-based intelligent library management system with a pioneering and innovative spirit. Through radio frequency identification technology, it will identify, track, and protect all the materials in the library, simplify the borrowing and returning processes of books, fully realize the intelligent management of library documents, effectively improve work efficiency and service levels, reform the old work concepts and methods. It will truly enable leaders to "come with expectations and leave satisfied", and significantly improve the service quality and image of the library.

RFID introduction
RFID is the abbreviation of Radio Frequency Identification, which is a non-contact automatic identification technology. In recent years, with the development of technologies such as large-scale integrated circuits, network communication, and information security, RFID has been rapidly applied to industries and fields such as smart grids, transportation, logistics and warehousing, medical and health care, asset management, finance and service industries, industrial and automatic control, smart homes, environmental and safety detection, public security, file management, national defense and military affairs, and smart cities. RFID technology is classified into low frequency, high frequency, ultra-high frequency, active 2.4G, etc. according to frequency bands. RFID technology has the characteristics of non-contact, fast scanning, high identification efficiency, being not easily damaged, being suitable for harsh environments, convenient operation, long reading distance, fast reading and writing speed, large information storage capacity, multi-purpose of one card, anti-collision, good security and encryption performance, reusability, tracking and positioning, etc.

RFID advantages
| Penetrability | Security | Data can be written |
|
RFID tags use wireless electromagnetic signals and can penetrate non-metallic objects such as plastics and wood.
|
The RFID electronic tag can be set with an access password/inactivation password, as well as data area locking/permanent locking.
|
The EPC (Electronic Product Code) of the tag and the user data area can have data rewritten up to 100,000 times.
|
|
Fast identification
|
Long reading distance
|
Improve inventory checking efficiency
|
|
The reading speed of tag identification is 200 tags per second.
|
The maximum reading distance of ordinary tags, flexible anti-metal tags and PCB anti-metal tags can reach up to 56 meters.
|
Barcode labels: 5-10 pieces per minute
RFID tags: 200 pieces per second
The efficiency is increased greatly.
|
Design logic

Overall Flow Chart of the Library Management System
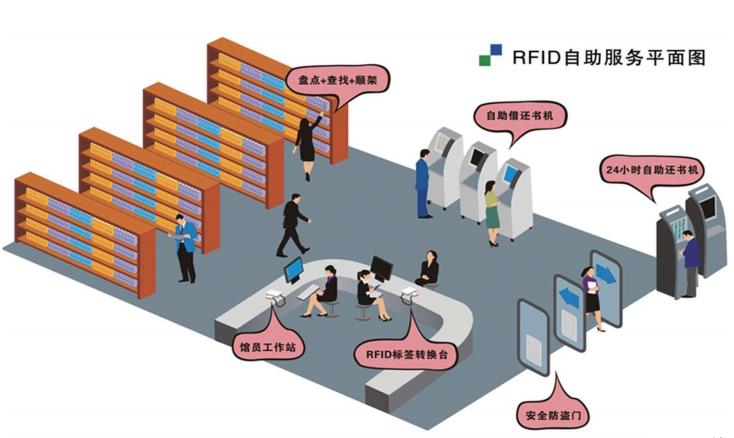
Principles of scheme design
|
The entire system should be easy to manage and maintain, with simple operation, and be easy to learn and use. It should facilitate system configuration, be well monitored and controlled in terms of equipment, security, data traffic, performance, etc., and support remote management and fault diagnosis.
|
The data of users on the information platform is their business secret, and data security is of utmost importance. Therefore, it is crucial to adopt advanced protection technologies such as authentication technology, key technology, and WEB secure access technology to enhance the security and confidentiality of the system.
|
The system provided by the platform should have the capabilities of error handling, fault tolerance, and redundant backup, and it should not lead to the paralysis of the entire system due to local failures.
|
| Principle of practicality |
Principle of security
|
Principle of reliability
|
|
Select products with advanced and mature technologies; the system planning and design should be of advanced nature. Adopt advanced concepts for system planning and design, as well as advanced computer software and hardware and network technologies for design and development.
|
Comply with common international or industry standards in all aspects, including system platform, network management, project management, and the formulation of system maintenance specifications. In this way, the system can support the interconnection of various heterogeneous platforms and different network protocols.
|
Business requirements will continue to evolve, and when the existing system fails to meet the application requirements, the system will face the need for renewal and replacement. Therefore, the design of the system must have a certain expansion capacity and leave room for upgrades to meet the needs of future business development.
|
| Principle of advancement | Principle of standardization | Principle of expandability |
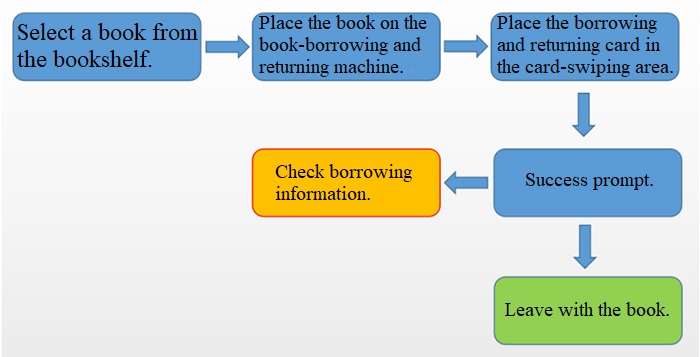
Easily achieve the function of self-service borrowing and returning
1)The reader places the library card in the identifiable area of the reader-writer on the desktop.
2)After the reader's identity is confirmed, the reader places the book(s) to be borrowed in the identifiable area of the reader-writer on the desktop. The reader-writer then starts to scan the book tags. During the scanning process, the book(s) should not be taken out of the reading and writing area.
3)After the reader-writer has finished scanning the book tags, it will display the results on the touch screen. The reader's book borrowing process is completed, and a list will be printed.
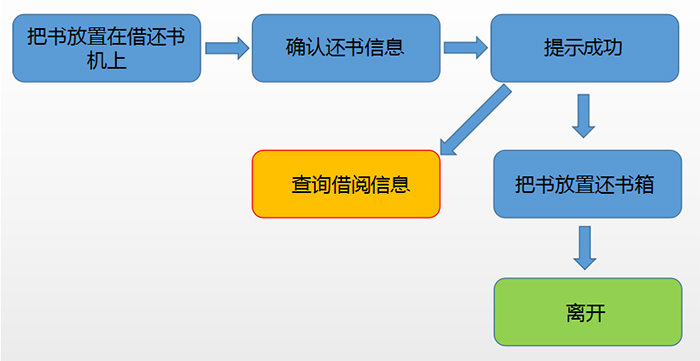
● Book returning procedure:
1)The reader places the book(s) to be returned in the identifiable area of the reader-writer on the desktop. The reader-writer then starts to scan the book tags. During the scanning process, the book(s) should not be taken out of the reading and writing area.
2) The reader confirms the book return. Once the successful return is displayed, the reader can simply place the book in the book return box.
Hardware supporting the system
The inventory device has a simple and elegant appearance. It is lightweight, small in size, and convenient and quick to carry. It can quickly position the shelf labels. By scanning the shelf labels pasted on the compact shelves and the electronic book labels, it can achieve functions such as shelf arrangement, data collection, searching, and statistics of circulated materials. It features a fast scanning speed, high accuracy, and reliability. Borrowing can be carried out according to reserved tasks, and it is very flexible to use.
 |
The label conversion device needs to be connected to a PC. It can quickly identify the book boxes with RFID tags and rapidly bind the label information. It is convenient to operate, and is designed to be waterproof and wear-resistant. It uses high-strength tempered glass. An ID card reader-writer and a barcode scanner can be optionally configured, enabling flexible use. It is also easy to install.
 |
The all-in-one machine for the librarian workstation adopts an integrated design, and its 21.5-inch screen makes the operation convenient. It can identify RFID tags and handle their circulation status. With the assistance of other devices, it enables the circulation department to quickly perform borrowing and returning operations on the circulated materials affixed with RFID tags and barcodes, thus improving the work efficiency of the staff.
 |
The equipment of the intelligent access control system can scan and conduct security identification on the books affixed with RFID tags, and is used for the real-time monitoring of the books leaving the library. This equipment system determines the status of each book (whether the borrowing procedures have been completed) that is carried close to the body or put into a backpack, so as to achieve the purposes of anti-theft and monitoring.
 |
The equipment of the self-service borrowing and returning system is an important component of the intelligent library. Through the background system, it scans and identifies the circulated materials affixed with electronic tags and barcodes. It is equipped with a touch display screen or a simple button operation system, providing a simple and easy-to-operate human-computer interaction interface and graphical interface, enabling the borrowing process to be completed quickly and accurately. This has significantly improved the work efficiency of the library.
 |
It is used to store the returned books. It is equipped with four universal pulleys and has a capacity of approximately 120 books. It has an internal lifting structure that can automatically lift and lower according to the load.
 |
It is a self-adhesive label. Once the label is properly pasted, it is not easy to be torn off or fall off. The label is pasted on the books to achieve the management of all books. It can effectively resist the interference of the original magnetic strips in the books. It has a high level of security to prevent the information stored in it from being leaked. It has a non-rewritable unique serial number (UID) for identification and encryption.
|
It is placed on each layer of the bookshelf. The label comes with single-sided self-adhesive, and it can be installed on the bookshelf by pasting. The layer number, shelf number, and the library logo can be printed on the layer position and shelf position labels. The label has a high level of security to prevent the information stored in it from being leaked. Users can customize the data format and content, and it has good data expandability. It has a non-rewritable unique serial number (UID) for identification and encryption.
|