About Zirgy
[+]

export@shzjsmart.cn

Address
3F, Building 1, 875 Qiuxing Road, Pudong New District, Shanghai
Introduction of RFID asset management system
RFID's remarkable features
 |
 |
Abundant data storage space A two-dimensional barcode can store a maximum of 2,725 digits. When letters are included, its storage capacity further decreases. In contrast, an RFID tag has a storage capacity exceeding 294, which is nearly ten thousand characters.
|
 |
 |
 |
Convenient reading Data can be read without the need for a light source and can even be read through outer packaging. In the case of passive tags, the maximum distance for remote reading and writing can reach up to 1.5 meters. When employing active tags equipped with built-in batteries, the effective identification range can surpass 30 meters. |
 |
Fast reading/writing It adopts a contactless method and has no directional requirements. Once the tag enters the magnetic field, the reader can immediately read the information in it. Usually, a read-write operation can be completed within a few milliseconds. The anti-collision mechanism employed enables it to process multiple tags simultaneously, achieving batch identification. |
 |
Anti-collision There is an anti-collision mechanism in the electronic tag, which can prevent data interference between cards. Therefore, the reader can process multiple contactless radio frequency cards "simultaneously", and it can handle more than 200 cards at a time. It does not require a light source and can even read data through external materials |
|||
 |
High data security RFID adopts the encoding system of the international unified Electronic Product Code (EPC). Before leaving the factory, a unique 40-bit identification internal code that is not repeated is solidified in the chip. This code cannot be replicated or modified. This technology is very difficult to be counterfeited or invaded. |
 |
Superior physical properties It can store both permanent and non-permanent data. The information in the rewritable memory can be changed freely. The data can be updated dynamically and replaced repeatedly (it can be erased and written 100,000 times, and read infinitely). It has a long service life (10 years or 100,000 times of reading and writing), can withstand high and low temperatures, and can adapt to various operating environments and conditions. |
Typical problems encountered in asset management

Anticipated goal


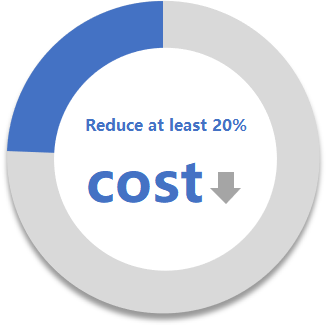
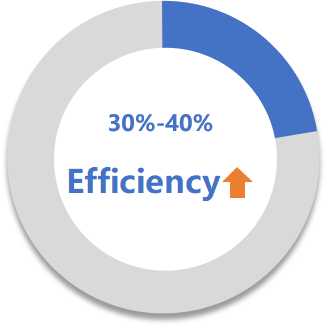
Multidimensional gain
 |
 |
 |
 |
 |
|
Elimination of paper-based processes Workforce optimization
Adoption of electronic waybills
Reduction in manual labor requirements
|
 |
Precise inventory monitoring Efficient exception handling Instant real-time inventory checking Rigorous entry and exit checks |
 |
Advanced system automation Clear-cut product visualization Seamless system invisibility Enhanced effectiveness optimization |
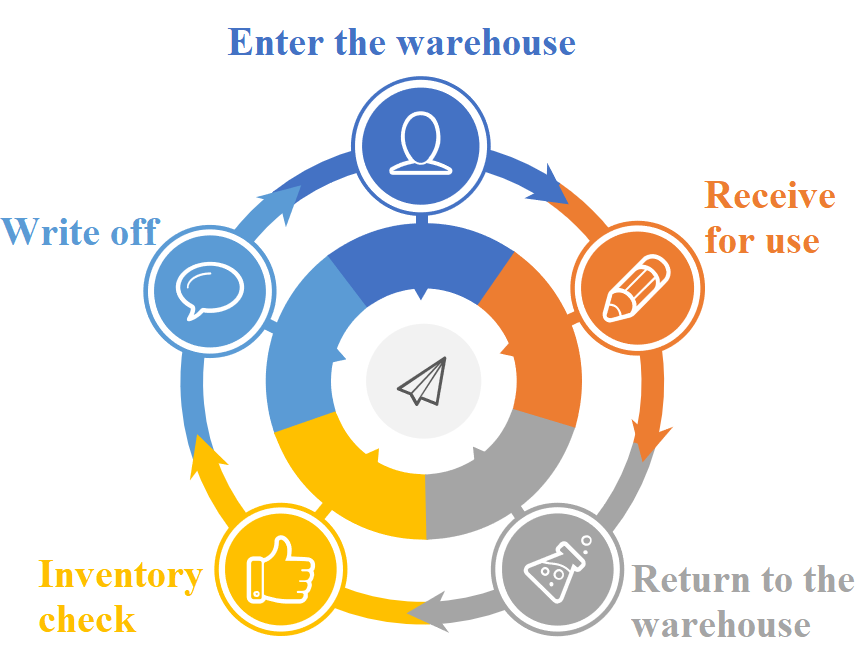
Full life cycle management of assets
| Monitor and record every operational action related to assets, enabling a comprehensive view of their life cycles. For each individual asset, document details including the operator, operation timestamp, user identity, usage department, and storage location, etc. |  |
 |
Supported platforms: PC, APP and mini-program
| The system supports three platforms: APP, PC, and mini-program. Different ports are used for operation according to the needs of different user groups. For example, the PC and APP terminals for managers integrate a variety of functions, which facilitate managers to respond in a timely manner. The functions of the mini-program terminal for employees are relatively vertical, meeting the employees' daily needs such as requisition and return to the warehouse. |  |
 |
Smart inbound procedure
|
Diverse methods and a rigorous process
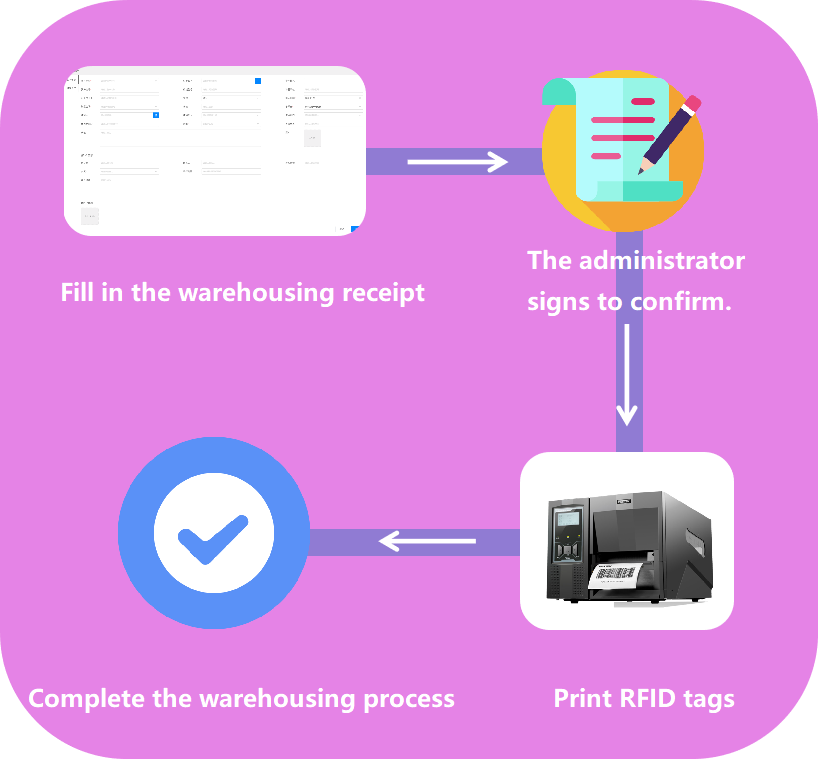
►Fill in the warehousing form to complete the asset warehousing.
►For existing assets, you can duplicate and create a new one to complete the quick warehousing. ►Administrator signatures can be set to ensure accuracy. ►After the assets are warehoused, click "Issue Card" to print the tag, and issue a unique ID for each asset. |
 |
 |
Unified management by binding multiple assets
|
Main assets bind subsidiary assets For assets with an affiliated relationship in daily life, when the assets are put into storage, the system can designate the assets being put into storage as the main assets, and bind other already-stored assets as subsidiary assets to these main assets. After binding, for operations such as asset requisition, borrowing, and return to storage, only by requisitioning the main asset can one directly obtain the subsidiary assets. The affiliated relationship can be changed in the subsidiary asset modification.
|
 |
 |
Customize the asset coding rules
|
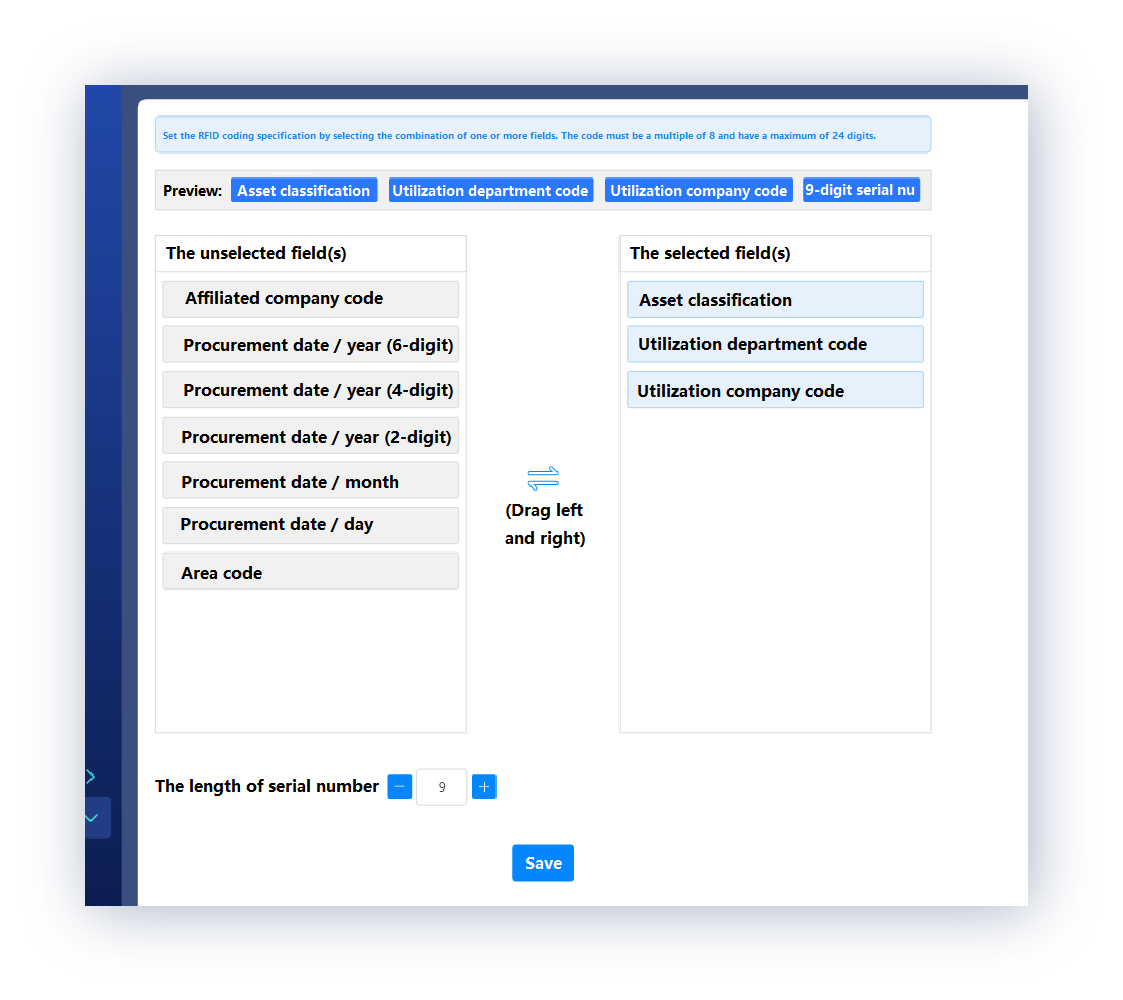
The code contains practical information.
The system supports users to customize the asset coding, enabling users to know the relevant information of the assets just by looking at the codes. At the same time, it can fully conform to the actual application scenarios according to the length of the customized serial number.
Asset coding: A + B + C + serial number
|
 |
 |
Intelligent requisition procedure
|
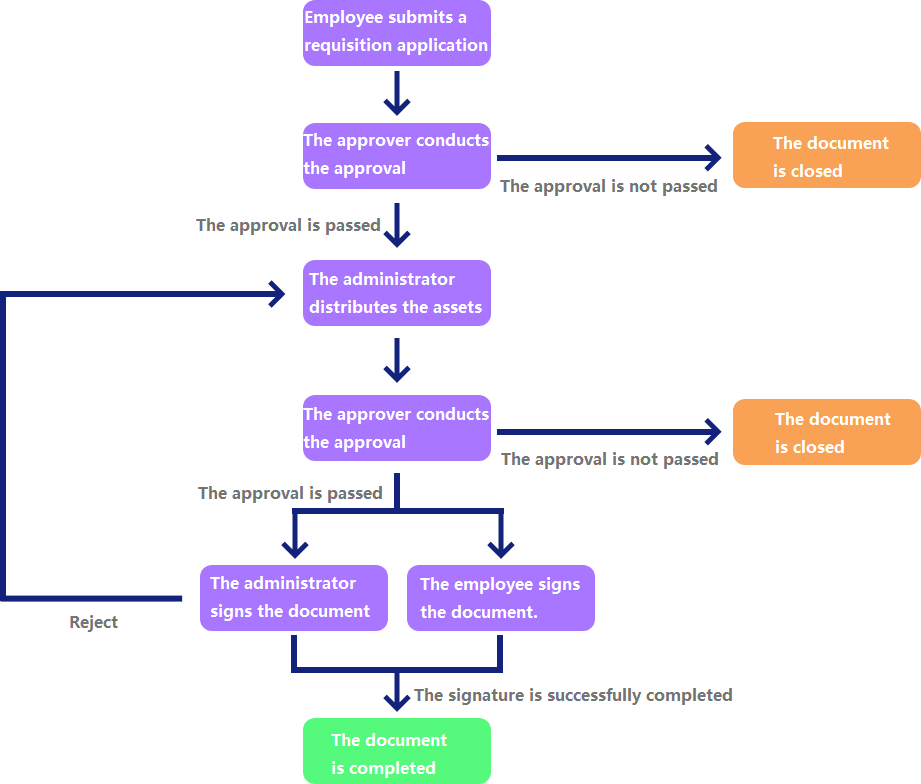
The approval and signature processes can be set freely. It perfectly meets the actual needs of users. |
 |
 |
Smart quick inventory checking
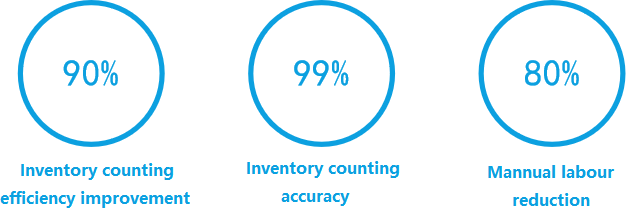
| Better effect The inventory checking methods using traditional barcodes or manual counting are inefficient; RFID inventory can enable a single person to conduct a rapid inventory. RFID inventory checking can also provide a more convenient means of detecting inventory checking accuracy.
Only one or two people are needed to conduct an inventory checking of a large warehouse.
 |
 |
 |
Comprehensive asset monitoring
|
Form the movement track of assets Record the time and location information of the assets at all the points they pass through. Multiple points are connected in series to form the movement track of assets. Prevent important documents from being taken out of the company. Comprehensive control of important documents Prevent the outflow in restricted areas Define the scope of asset activities Customize and set the asset monitoring area. Complete the detailed division of the asset activity areas in coordination with the multi-level area settings. |
 |
 |
Multi-dimensional analysis statements
| Generate various reports required by users through data integration. The system provides a variety of data statistical reports according to the actual needs of users. Corresponding conclusions can be drawn through the summarization of data, which facilitates the management to make decisions. |
 |
 |
Multifaceted automatic reminder
| Exit monitoring area alert Assets that are not compliant outside the monitoring area Loan return reminder Assets that have not been returned by the expected time of return Asset maturity reminder Assets whose useful life has expired Reminder of assets that expire in the current month Maintenance of assets maturing this month Pending task Tasks that the administrator needs to approve but does not approve |
 |
 |
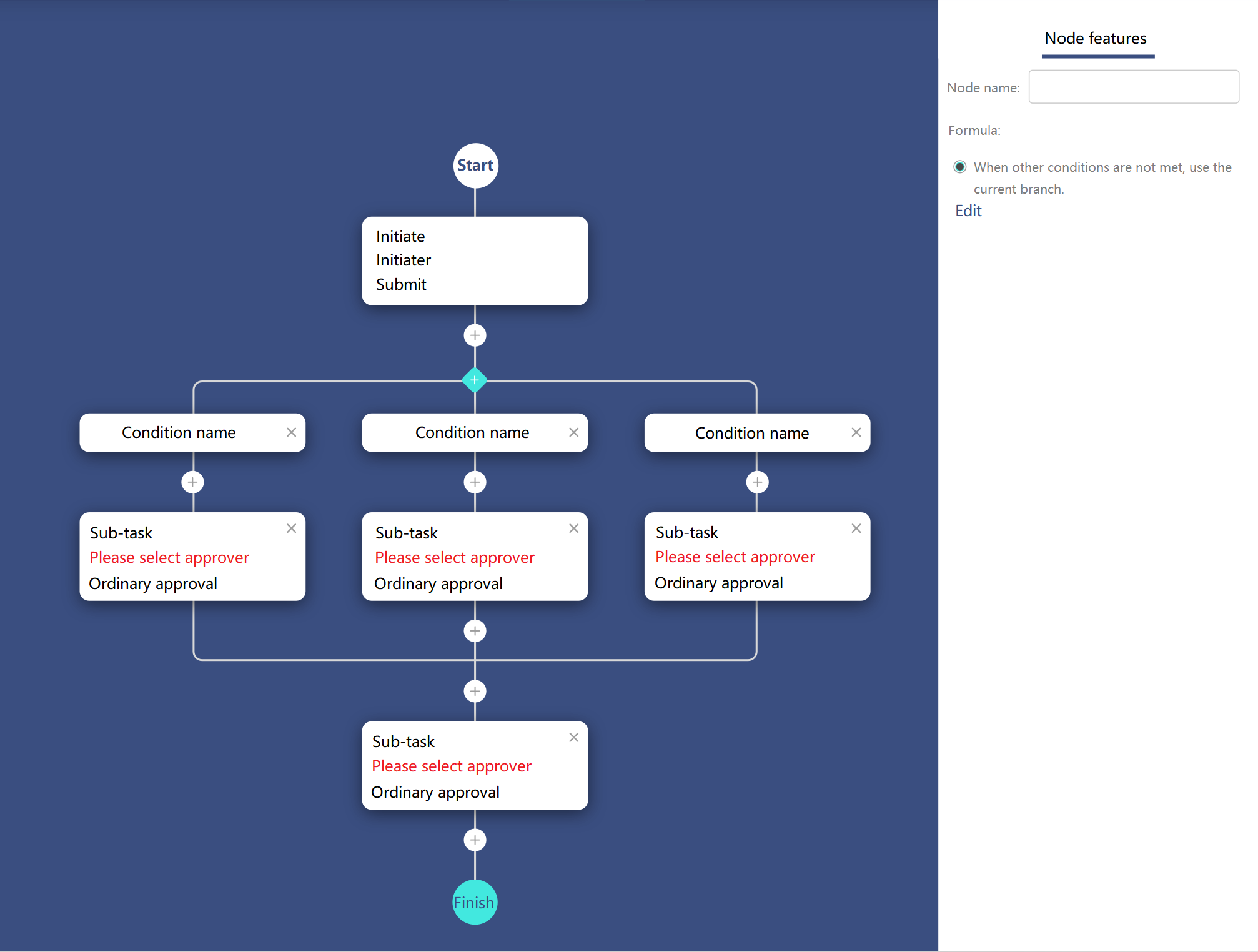
Customized approval process
|
Customize the approval process and customize the way you need it most
|
 |
 |
Full monitoring without dead ends
Application and approval process All operations require operation application and approval management Ensure accurate operation and compliance Reminder, alarm management Remind of asset borrowing, maintenance, expiration, etc Alarm for departure from monitoring area Home page signage Display the asset status proportion, asset classification statistics, and regional asset statistics Show the proportion of company use and department use |
 |
 |
Applicable industry
 |
 |
 |
 |
 |
 |
 |
 |
||
 |
 |
 |
||
 |
 |
 |